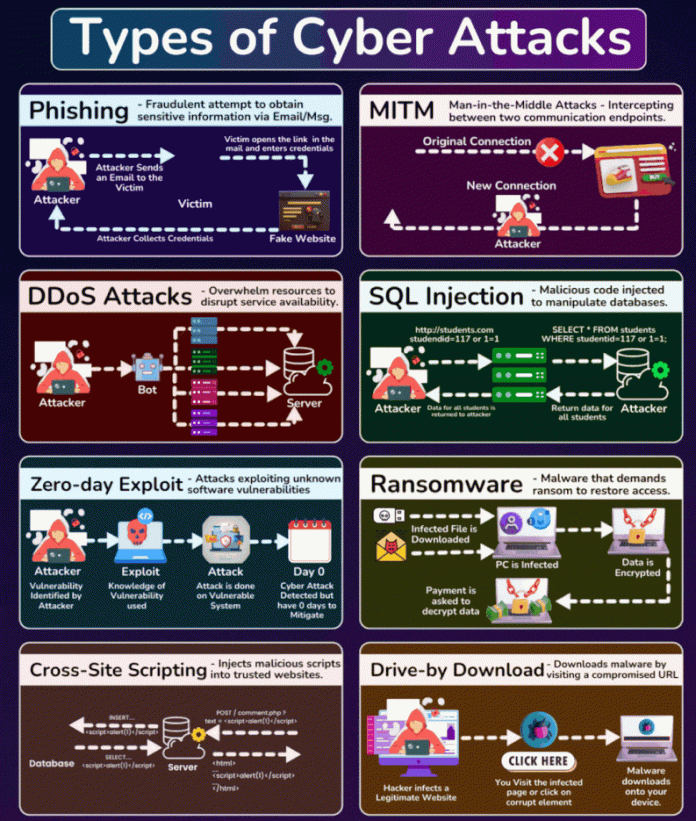
Let’s face it — we live in a world where clicking the wrong link can cost you a paycheck, a server meltdown, or worse… your weekend. Whether you’re running a business, coding your next SaaS, or just trying to check your email without a digital ambush — knowing your cyber foes is half the battle.
Here are 8 of the most common cyber attacks and how to slap some digital armor on yourself.
1. 🎣 Phishing – Hook, Line, and Sinker
What it is: A sneaky message, often email or SMS, that pretends to be legit and lures you into giving up your credentials.
Common Targets: Logins, credit cards, employee portals.
Defense Plan:
Think before you click.
Check the sender address like it’s a bad alibi.
Enable Multi-Factor Authentication (MFA).
Train your team — because one click can sink the whole ship.
2. 🕵️♂️ MITM (Man-in-the-Middle) – Digital Eavesdropping
What it is: A hacker gets between your communication (like Wi-Fi snooping) to steal data.
Common Targets: Logins, financial transactions.
Defense Plan:
Always use HTTPS websites.
Avoid public Wi-Fi without a VPN.
Encrypt your communications.
3. 🧨 DDoS Attacks – When Traffic Becomes a Weapon
What it is: Overloading a website or server with junk traffic so it crashes or becomes useless.
Common Targets: eCommerce, SaaS platforms, game servers.
Defense Plan:
Use a CDN and firewall (e.g., Cloudflare, AWS Shield).
Rate-limit traffic.
Monitor network spikes like a hawk on Red Bull.
4. 🧬 SQL Injection – Talk Dirty to the Database
What it is: Hackers inject malicious queries into forms or URLs to manipulate your database.
Common Targets: Login forms, search boxes, admin panels.
Defense Plan:
Sanitize and validate all inputs.
Use parameterized SQL queries (prepared statements).
Never trust user input — it’s not your friend.
5. 🕳️ Zero-Day Exploit – Attack Before the Patch
What it is: A flaw in software that no one (except the attacker) knows about — until it’s too late.
Common Targets: Operating systems, browsers, WordPress plugins.
Defense Plan:
Keep software updated — seriously.
Use threat intelligence feeds.
Deploy endpoint protection with behavioral detection.
6. 🧨 Ransomware – Digital Kidnapping
What it is: Malware that encrypts your files and demands payment to unlock them.
Common Targets: Small businesses, hospitals, city governments.
Defense Plan:
Back. It. Up. (And keep a copy offline.)
Train staff to avoid infected attachments.
Segment your network to contain outbreaks.
7. 💉 Cross-Site Scripting (XSS) – Script Kiddies Gone Wild
What it is: Attackers inject scripts into websites that then run in a visitor’s browser.
Common Targets: Comments sections, profile fields, search bars.
Defense Plan:
Escape output, not just input.
Use a Content Security Policy (CSP).
Test your app like it owes you money.
8. 🚨 Drive-By Downloads – One Click and You’re Doomed
What it is: Malware installs automatically when you visit a compromised or fake website.
Common Targets: Any browser with outdated plugins or users who click “FREE IPAD!”
Defense Plan:
Keep your browser and plugins updated.
Run real-time antivirus.
Disable Flash — this isn’t 2003.
Final Thoughts from the Tech Forest 🍄
Cybersecurity isn’t just for IT nerds or SOC analysts. It’s for you, the entrepreneur, the remote worker, the creative, the digital hustler.
Every click, every upload, and every form field is a potential opening.
But with knowledge, a solid plan, and the right mindset, you become unhackable (okay, mostly).